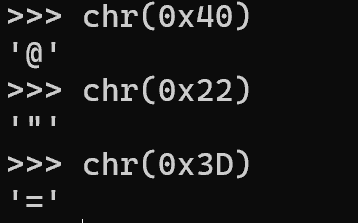
.text:004021DD
.text:004021DD ; =============== S U B R O U T I N E =======================================
.text:004021DD
.text:004021DD ; Attributes: bp-based frame fuzzy-sp
.text:004021DD
.text:004021DD ; int __cdecl main(int argc, const char **argv, const char **envp)
.text:004021DD public main
.text:004021DD main proc near ; DATA XREF: .got:main_ptr↓o
.text:004021DD
.text:004021DD src = byte ptr -6Ch
.text:004021DD var_4 = dword ptr -4
.text:004021DD argc = dword ptr 8
.text:004021DD argv = dword ptr 0Ch
.text:004021DD envp = dword ptr 10h
.text:004021DD
.text:004021DD ; __unwind {
.text:004021DD lea ecx, [esp+4]
.text:004021E1 and esp, 0FFFFFFF0h
.text:004021E4 push dword ptr [ecx-4]
.text:004021E7 push ebp
.text:004021E8 mov ebp, esp
.text:004021EA push ecx
.text:004021EB sub esp, 74h
.text:004021EE sub esp, 0Ch
.text:004021F1 push offset format ; "please input your flag:"
.text:004021F6 call printf
.text:004021FB add esp, 10h
.text:004021FE sub esp, 8
.text:00402201 lea eax, [ebp+src]
.text:00402204 push eax
.text:00402205 push offset a19s ; "%19s"
.text:0040220A call __isoc99_scanf
.text:0040220F add esp, 10h
.text:00402212 sub esp, 0Ch
.text:00402215 lea eax, [ebp+src]
.text:00402218 push eax
.text:00402219 call function2
.text:0040221E add esp, 10h
.text:00402221 sub esp, 0Ch
.text:00402224 lea eax, [ebp+src]
.text:00402227 push eax ; src
.text:00402228 call function0
.text:0040222D add esp, 10h
.text:00402230 mov eax, 0
.text:00402235 mov ecx, [ebp+var_4]
.text:00402238 leave
.text:00402239 lea esp, [ecx-4]
.text:0040223C retn
.text:0040223C ; } // starts at 4021DD
.text:0040223C main endp
.text:0040223C
.text:0040223D
.text:0040223D ; =============== S U B R O U T I N E =======================================
.text:0040223D
.text:0040223D ; Attributes: noreturn bp-based frame
.text:0040223D
.text:0040223D public function1
.text:0040223D function1 proc near
.text:0040223D
.text:0040223D var_1F = dword ptr -1Fh
.text:0040223D var_1B = dword ptr -1Bh
.text:0040223D var_17 = byte ptr -17h
.text:0040223D var_16 = byte ptr -16h
.text:0040223D var_C = dword ptr -0Ch
.text:0040223D
.text:0040223D ; __unwind {
.text:0040223D push ebp
.text:0040223E mov ebp, esp
.text:00402240 sub esp, 28h
.text:00402243 mov [ebp+var_1F], 4D626D41h
.text:0040224A mov [ebp+var_1B], 294E4953h
.text:00402251 mov [ebp+var_17], 28h ; '('
.text:00402255 sub esp, 0Ch
.text:00402258 push offset s ; "hhh,you find me:"
.text:0040225D call puts
.text:00402262 add esp, 10h
.text:00402265 sub esp, 8
.text:00402268 lea eax, [ebp+var_16]
.text:0040226B push eax
.text:0040226C push offset aS ; "%s"
.text:00402271 call __isoc99_scanf
.text:00402276 add esp, 10h
.text:00402279 mov [ebp+var_C], 0
.text:00402280 jmp short loc_4022B5
.text:00402282 ; ---------------------------------------------------------------------------
.text:00402282
.text:00402282 loc_402282: ; CODE XREF: function1+7C↓j
.text:00402282 lea edx, [ebp+var_16]
.text:00402285 mov eax, [ebp+var_C]
.text:00402288 add eax, edx
.text:0040228A movzx eax, byte ptr [eax]
.text:0040228D movsx eax, al
.text:00402290 sub eax, [ebp+var_C]
.text:00402293 mov edx, eax
.text:00402295 lea ecx, [ebp+var_1F]
.text:00402298 mov eax, [ebp+var_C]
.text:0040229B add eax, ecx
.text:0040229D movzx eax, byte ptr [eax]
.text:004022A0 movsx eax, al
.text:004022A3 cmp edx, eax
.text:004022A5 jz short loc_4022B1
.text:004022A7 sub esp, 0Ch
.text:004022AA push 0 ; status
.text:004022AC call exit
.text:004022B1 ; ---------------------------------------------------------------------------
.text:004022B1
.text:004022B1 loc_4022B1: ; CODE XREF: function1+68↑j
.text:004022B1 add [ebp+var_C], 1
.text:004022B5
.text:004022B5 loc_4022B5: ; CODE XREF: function1+43↑j
.text:004022B5 cmp [ebp+var_C], 8
.text:004022B9 jle short loc_402282
.text:004022BB sub esp, 0Ch
.text:004022BE push offset aCongratulate ; "congratulate!!!"
.text:004022C3 call puts
.text:004022C8 add esp, 10h
.text:004022CB sub esp, 0Ch
.text:004022CE push 0 ; status
.text:004022D0 call exit
.text:004022D0 ; } // starts at 40223D
.text:004022D0 function1 endp
.text:004022D0
.text:004022D5
.text:004022D5 ; =============== S U B R O U T I N E =======================================
.text:004022D5
.text:004022D5 ; Attributes: bp-based frame
.text:004022D5
.text:004022D5 ; int __cdecl function0(char *src)
.text:004022D5 public function0
.text:004022D5 function0 proc near ; CODE XREF: main+4B↑p
.text:004022D5
.text:004022D5 dest = byte ptr -0Ch
.text:004022D5 src = dword ptr 8
.text:004022D5
.text:004022D5 ; __unwind {
.text:004022D5 push ebp
.text:004022D6 mov ebp, esp
.text:004022D8 sub esp, 18h
.text:004022DB sub esp, 8
.text:004022DE push [ebp+src] ; src
.text:004022E1 lea eax, [ebp+dest]
.text:004022E4 push eax ; dest
.text:004022E5 call strcpy
.text:004022EA add esp, 10h
.text:004022ED mov eax, 0
.text:004022F2 leave
.text:004022F3 retn
.text:004022F3 ; } // starts at 4022D5
.text:004022F3 function0 endp
.text:004022F3
.text:004022F4
.text:004022F4 ; =============== S U B R O U T I N E =======================================
.text:004022F4
.text:004022F4 ; Attributes: bp-based frame
.text:004022F4
.text:004022F4 ; int __cdecl function2(int)
.text:004022F4 public function2
.text:004022F4 function2 proc near ; CODE XREF: main+3C↑p
.text:004022F4
.text:004022F4 var_1C = dword ptr -1Ch
.text:004022F4 var_18 = dword ptr -18h
.text:004022F4 var_14 = dword ptr -14h
.text:004022F4 var_10 = dword ptr -10h
.text:004022F4 var_C = dword ptr -0Ch
.text:004022F4 arg_0 = dword ptr 8
.text:004022F4
.text:004022F4 ; __unwind {
.text:004022F4 push ebp
.text:004022F5 mov ebp, esp
.text:004022F7 sub esp, 28h
.text:004022FA mov [ebp+var_1C], 65575A2Fh
.text:00402301 mov [ebp+var_18], 0CD698F14h
.text:00402308 mov [ebp+var_14], 551A2993h
.text:0040230F mov [ebp+var_10], 5EE44018h
.text:00402316 push 10h
.text:00402318 push [ebp+arg_0]
.text:0040231B push 5
.text:0040231D push offset aSuctf ; "suctf"
.text:00402322 call function5
.text:00402327 add esp, 10h
.text:0040232A mov [ebp+var_C], 0
.text:00402331 jmp short loc_402364
.text:00402333 ; ---------------------------------------------------------------------------
.text:00402333
.text:00402333 loc_402333: ; CODE XREF: function2+74↓j
.text:00402333 mov edx, [ebp+var_C]
.text:00402336 mov eax, [ebp+arg_0]
.text:00402339 add eax, edx
.text:0040233B movzx eax, byte ptr [eax]
.text:0040233E movsx eax, al
.text:00402341 movzx edx, al
.text:00402344 lea ecx, [ebp+var_1C]
.text:00402347 mov eax, [ebp+var_C]
.text:0040234A add eax, ecx
.text:0040234C movzx eax, byte ptr [eax]
.text:0040234F movzx eax, al
.text:00402352 cmp edx, eax
.text:00402354 jz short loc_402360
.text:00402356 sub esp, 0Ch
.text:00402359 push 0 ; status
.text:0040235B call exit
.text:00402360 ; ---------------------------------------------------------------------------
.text:00402360
.text:00402360 loc_402360: ; CODE XREF: function2+60↑j
.text:00402360 add [ebp+var_C], 1
.text:00402364
.text:00402364 loc_402364: ; CODE XREF: function2+3D↑j
.text:00402364 cmp [ebp+var_C], 0Fh
.text:00402368 jle short loc_402333
.text:0040236A nop
.text:0040236B nop
.text:0040236C leave
.text:0040236D retn
.text:0040236D ; } // starts at 4022F4
.text:0040236D function2 endp
.text:0040236D
.text:0040236E
.text:0040236E ; =============== S U B R O U T I N E =======================================
.text:0040236E
.text:0040236E ; Attributes: bp-based frame
.text:0040236E
.text:0040236E ; int __cdecl function3(int, int, int)
.text:0040236E public function3
.text:0040236E function3 proc near ; CODE XREF: function5+16↓p
.text:0040236E
.text:0040236E var_9 = byte ptr -9
.text:0040236E var_8 = dword ptr -8
.text:0040236E var_4 = dword ptr -4
.text:0040236E arg_0 = dword ptr 8
.text:0040236E arg_4 = dword ptr 0Ch
.text:0040236E arg_8 = dword ptr 10h
.text:0040236E
.text:0040236E ; __unwind {
.text:0040236E push ebp
.text:0040236F mov ebp, esp
.text:00402371 sub esp, 10h
.text:00402374 mov [ebp+var_8], 0
.text:0040237B mov [ebp+var_4], 0
.text:00402382 jmp short loc_402395
.text:00402384 ; ---------------------------------------------------------------------------
.text:00402384
.text:00402384 loc_402384: ; CODE XREF: function3+2E↓j
.text:00402384 mov edx, [ebp+var_4]
.text:00402387 mov eax, [ebp+arg_8]
.text:0040238A add eax, edx
.text:0040238C mov edx, [ebp+var_4]
.text:0040238F mov [eax], dl
.text:00402391 add [ebp+var_4], 1
.text:00402395
.text:00402395 loc_402395: ; CODE XREF: function3+14↑j
.text:00402395 cmp [ebp+var_4], 0FFh
.text:0040239C jle short loc_402384
.text:0040239E mov [ebp+var_4], 0
.text:004023A5 jmp short loc_402416
.text:004023A7 ; ---------------------------------------------------------------------------
.text:004023A7
.text:004023A7 loc_4023A7: ; CODE XREF: function3+AF↓j
.text:004023A7 mov edx, [ebp+var_4]
.text:004023AA mov eax, [ebp+arg_8]
.text:004023AD add eax, edx
.text:004023AF movzx eax, byte ptr [eax]
.text:004023B2 movzx edx, al
.text:004023B5 mov eax, [ebp+var_8]
.text:004023B8 lea ecx, [edx+eax]
.text:004023BB mov eax, [ebp+var_4]
.text:004023BE cdq
.text:004023BF idiv [ebp+arg_4]
.text:004023C2 mov eax, edx
.text:004023C4 mov edx, eax
.text:004023C6 mov eax, [ebp+arg_0]
.text:004023C9 add eax, edx
.text:004023CB movzx eax, byte ptr [eax]
.text:004023CE movzx eax, al
.text:004023D1 add eax, ecx
.text:004023D3 cdq
.text:004023D4 shr edx, 18h
.text:004023D7 add eax, edx
.text:004023D9 movzx eax, al
.text:004023DC sub eax, edx
.text:004023DE mov [ebp+var_8], eax
.text:004023E1 mov edx, [ebp+var_4]
.text:004023E4 mov eax, [ebp+arg_8]
.text:004023E7 add eax, edx
.text:004023E9 movzx eax, byte ptr [eax]
.text:004023EC mov [ebp+var_9], al
.text:004023EF mov edx, [ebp+var_8]
.text:004023F2 mov eax, [ebp+arg_8]
.text:004023F5 add eax, edx
.text:004023F7 mov ecx, [ebp+var_4]
.text:004023FA mov edx, [ebp+arg_8]
.text:004023FD add edx, ecx
.text:004023FF movzx eax, byte ptr [eax]
.text:00402402 mov [edx], al
.text:00402404 mov edx, [ebp+var_8]
.text:00402407 mov eax, [ebp+arg_8]
.text:0040240A add edx, eax
.text:0040240C movzx eax, [ebp+var_9]
.text:00402410 mov [edx], al
.text:00402412 add [ebp+var_4], 1
.text:00402416
.text:00402416 loc_402416: ; CODE XREF: function3+37↑j
.text:00402416 cmp [ebp+var_4], 0FFh
.text:0040241D jle short loc_4023A7
.text:0040241F nop
.text:00402420 nop
.text:00402421 leave
.text:00402422 retn
.text:00402422 ; } // starts at 40236E
.text:00402422 function3 endp
.text:00402422
.text:00402423
.text:00402423 ; =============== S U B R O U T I N E =======================================
.text:00402423
.text:00402423 ; Attributes: bp-based frame
.text:00402423
.text:00402423 ; int __cdecl function4(int, int, int)
.text:00402423 public function4
.text:00402423 function4 proc near ; CODE XREF: function5+2B↓p
.text:00402423
.text:00402423 var_14 = dword ptr -14h
.text:00402423 var_D = byte ptr -0Dh
.text:00402423 var_C = dword ptr -0Ch
.text:00402423 var_8 = dword ptr -8
.text:00402423 var_4 = dword ptr -4
.text:00402423 arg_0 = dword ptr 8
.text:00402423 arg_4 = dword ptr 0Ch
.text:00402423 arg_8 = dword ptr 10h
.text:00402423
.text:00402423 ; __unwind {
.text:00402423 push ebp
.text:00402424 mov ebp, esp
.text:00402426 sub esp, 20h
.text:00402429 mov [ebp+var_4], 0
.text:00402430 mov [ebp+var_8], 0
.text:00402437 mov [ebp+var_C], 0
.text:0040243E jmp loc_4024F6
.text:00402443 ; ---------------------------------------------------------------------------
.text:00402443
.text:00402443 loc_402443: ; CODE XREF: function4+D9↓j
.text:00402443 mov eax, [ebp+var_4]
.text:00402446 add eax, 1
.text:00402449 cdq
.text:0040244A shr edx, 18h
.text:0040244D add eax, edx
.text:0040244F movzx eax, al
.text:00402452 sub eax, edx
.text:00402454 mov [ebp+var_4], eax
.text:00402457 mov edx, [ebp+var_4]
.text:0040245A mov eax, [ebp+arg_0]
.text:0040245D add eax, edx
.text:0040245F movzx eax, byte ptr [eax]
.text:00402462 movzx edx, al
.text:00402465 mov eax, [ebp+var_8]
.text:00402468 add eax, edx
.text:0040246A cdq
.text:0040246B shr edx, 18h
.text:0040246E add eax, edx
.text:00402470 movzx eax, al
.text:00402473 sub eax, edx
.text:00402475 mov [ebp+var_8], eax
.text:00402478 mov edx, [ebp+var_4]
.text:0040247B mov eax, [ebp+arg_0]
.text:0040247E add eax, edx
.text:00402480 movzx eax, byte ptr [eax]
.text:00402483 mov [ebp+var_D], al
.text:00402486 mov edx, [ebp+var_8]
.text:00402489 mov eax, [ebp+arg_0]
.text:0040248C add eax, edx
.text:0040248E mov ecx, [ebp+var_4]
.text:00402491 mov edx, [ebp+arg_0]
.text:00402494 add edx, ecx
.text:00402496 movzx eax, byte ptr [eax]
.text:00402499 mov [edx], al
.text:0040249B mov edx, [ebp+var_8]
.text:0040249E mov eax, [ebp+arg_0]
.text:004024A1 add edx, eax
.text:004024A3 movzx eax, [ebp+var_D]
.text:004024A7 mov [edx], al
.text:004024A9 mov edx, [ebp+var_4]
.text:004024AC mov eax, [ebp+arg_0]
.text:004024AF add eax, edx
.text:004024B1 movzx edx, byte ptr [eax]
.text:004024B4 mov ecx, [ebp+var_8]
.text:004024B7 mov eax, [ebp+arg_0]
.text:004024BA add eax, ecx
.text:004024BC movzx eax, byte ptr [eax]
.text:004024BF add eax, edx
.text:004024C1 movzx edx, al
.text:004024C4 mov eax, [ebp+arg_0]
.text:004024C7 add eax, edx
.text:004024C9 movzx eax, byte ptr [eax]
.text:004024CC movzx eax, al
.text:004024CF mov [ebp+var_14], eax
.text:004024D2 mov edx, [ebp+var_C]
.text:004024D5 mov eax, [ebp+arg_4]
.text:004024D8 add eax, edx
.text:004024DA movzx eax, byte ptr [eax]
.text:004024DD mov edx, eax
.text:004024DF mov eax, [ebp+var_14]
.text:004024E2 mov ecx, edx
.text:004024E4 xor ecx, eax
.text:004024E6 mov edx, [ebp+var_C]
.text:004024E9 mov eax, [ebp+arg_4]
.text:004024EC add eax, edx
.text:004024EE mov edx, ecx
.text:004024F0 mov [eax], dl
.text:004024F2 add [ebp+var_C], 1
.text:004024F6
.text:004024F6 loc_4024F6: ; CODE XREF: function4+1B↑j
.text:004024F6 mov eax, [ebp+var_C]
.text:004024F9 cmp eax, [ebp+arg_8]
.text:004024FC jl loc_402443
.text:00402502 nop
.text:00402503 nop
.text:00402504 leave
.text:00402505 retn
.text:00402505 ; } // starts at 402423
.text:00402505 function4 endp
.text:00402505
.text:00402506
.text:00402506 ; =============== S U B R O U T I N E =======================================
.text:00402506
.text:00402506 ; Attributes: bp-based frame
.text:00402506
.text:00402506 public function5
.text:00402506 function5 proc near ; CODE XREF: function2+2E↑p
.text:00402506
.text:00402506 var_100 = byte ptr -100h
.text:00402506 arg_0 = dword ptr 8
.text:00402506 arg_4 = dword ptr 0Ch
.text:00402506 arg_8 = dword ptr 10h
.text:00402506 arg_C = dword ptr 14h
.text:00402506
.text:00402506 ; __unwind {
.text:00402506 push ebp
.text:00402507 mov ebp, esp
.text:00402509 sub esp, 100h
.text:0040250F lea eax, [ebp+var_100]
.text:00402515 push eax
.text:00402516 push [ebp+arg_4]
.text:00402519 push [ebp+arg_0]
.text:0040251C call function3
.text:00402521 add esp, 0Ch
.text:00402524 push [ebp+arg_C]
.text:00402527 push [ebp+arg_8]
.text:0040252A lea eax, [ebp+var_100]
.text:00402530 push eax
.text:00402531 call function4
.text:00402536 add esp, 0Ch
.text:00402539 nop
.text:0040253A leave
.text:0040253B retn
.text:0040253B ; } // starts at 402506
.text:0040253B function5 endp
.text:0040253B
.text:0040253B _text ends
.text:0040253B
.fini:0040253C ; ===========================================================================
.fini:0040253C
|
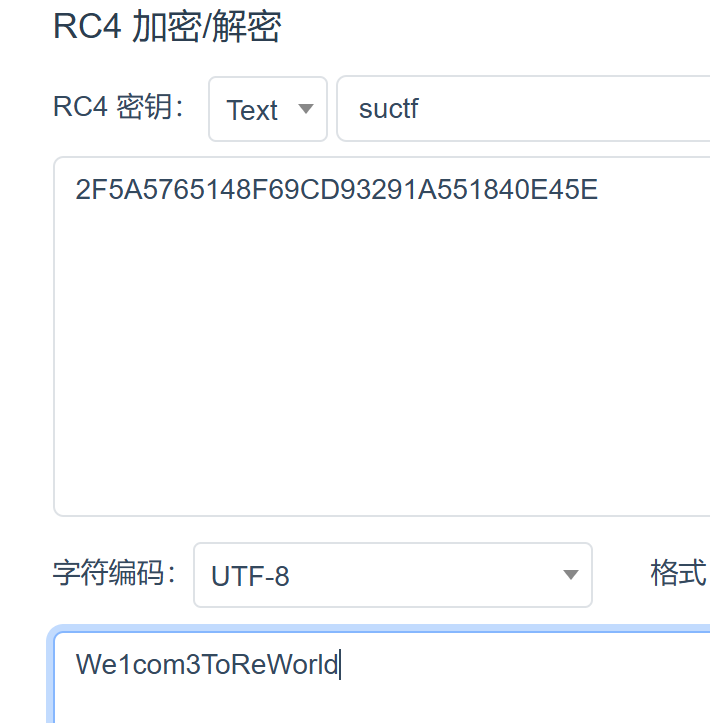 一个有语义的字符串,应该是flag的一部分,再回到程序本身,一共5个
一个有语义的字符串,应该是flag的一部分,再回到程序本身,一共5个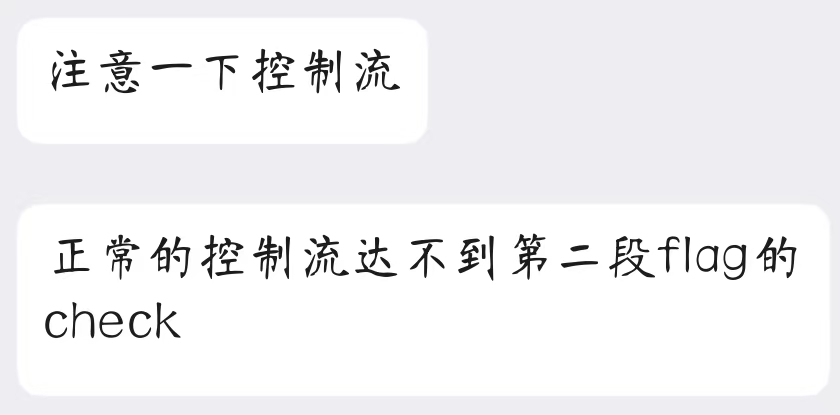 我们可以回想一下,main函数的
我们可以回想一下,main函数的